NMAP PROGRAM USING REFERENCE
Nmap is abbreviation of Network Mapper. Its was created in 1997 by Gordon Lyon as known as Phyodor Vaskovich in social
This program used for detecting host which connected with computer, service and to create network mapping. It is one of the best security programs for sending specially prepared and created network packet to the host and got information by analysing on the response. Initially, it was made for working on Linux, during the development gave a chance to work on Windows, Solaris, HP-UX,BSD , Mac Os, AmigOS, IRIX and UNIX. First version was made. in September 1997. It was written on C, C++ Python, Lua program language and works on many platform. It developed under GPL V2 license
Nmap program advantages:
- Host information – Detect hosts connected to network.
- Port examine – To show open ports of present host.
- Detect version – Detect application name, version number and the service working on network
- Detect operating system – Detect operation system and network equipment technical support information
- Audit – Detect network equipment, fire wall and network connection and auditing
- Collect informarion based on script - Collect information about present host, service and its interaction using NSE (Nmap Script Engine) and Lia program language.
- Create network registration and network mapping
- Create traffic on host and analyzing on the response
- Detecting new servers and auditing network security
- Decet network vulnerability and search exploit on it
Graphic interface:
First official Nmap customer graphic interface version was developed 2.2 version to 4.2 version and named NmapFE. It was written by Zach Smith. Afterwards, it was changed to Zenmap GUI developed by Adraiano Monteiro Marques. Also customers graphic interface versions had been using which based on web browser such as Nmap-web Nmap-CGI, LOCALSCAN, NmapWin.
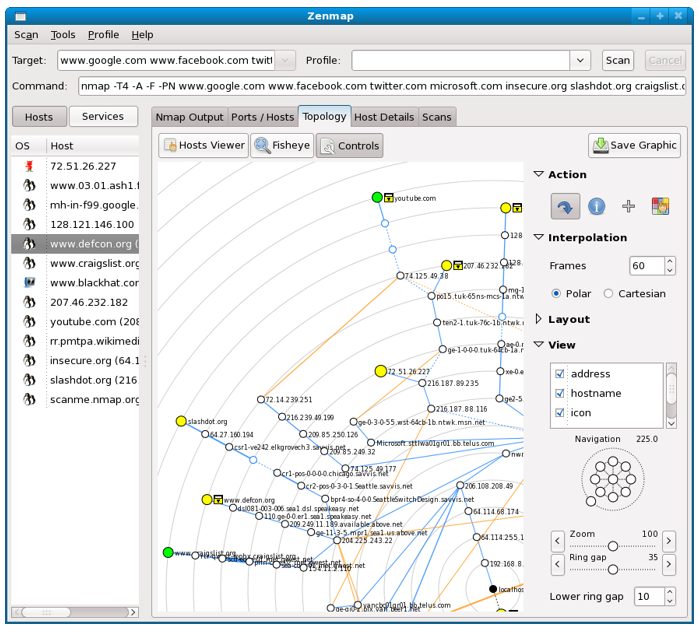
Picure 1. Zenmap
Exam result report of Nmap program:
However, Nmap supports 4 basic types of format it is able to save all results in file from output and it gives opportunity for customer to fix output result.
-
Interactive - Real time shows Nmap result where working on comand line.
- XML- Using xml additions print as xml format also using XSLT addition gives opportunity to write in html file.
-
Grepable - It`s able to control output using sed awk grep which is used on the comand line.
-
Normal - However, it is similar to interactive output, result output wrote on the file.
- Script kiddie - It transfered normal output into LEET script.
Nmap development chronological order
Nmap first version was published on Phrack Magazine with source code in September 1997. Since then, computer security community had supported and development had been made. First version was written on C, C++ language, furthermore it had functions such as detecting operation system and spotting.
- 1998.12.12 – Nmap 2.00 version was created, it included operating system spotting function.
- 1999.04.11 – NampFE interface added on Nmap
- 2000.12.07 – Started supporting windows operating system
- 2002.08.28 – Source code transferred C language into C++
- 2003.09.13 – Service version detector inserted first addition
- 22004.08.31 – Rewritten on basic “Core scan engine 3.70” version, was named ultra_scan
- 2005 summer – As a result Nmap involved Google summer of Code activity Zenmap,NSE, Ncat, second generation operating system detector was developed in addition.
- 2007.12.13 – Nmap 4.50 version created on 10th anniversary. For this version Zenmap, second generation operating system detector and Nmap Scripting Engine was officilay added on it.
- 2009.03.30 – Nmap 4.85 BETA 5 version created and it included Conficker infections detector in NSE resource.
- 2009.07.16 – Ncat, Ndiff examiner was exchanged to netcat option.
- 2011.01.28 – 5.50 version created, it included Nping.
- 2012.05.21 – 6.00 version created, it included all IPv6 support. At that time program total capacity was 54MB, 3572 OS fingerprints, 8165 version detector and 348 NSE scripts were included.
- 2015.11.09 – Nmap 7.0 version created.
- 2016.12.20 – Nmap 7.4 version created .
Nmap future orientation
Nmap had implemented so many projects, solution, and trends successfully in 20 years history. As developers said there will be no certain project, plan until new innovation of the internet, network technology, new technology that worldwide would follow and implement. As they expressed, generally they will provide IPv6 security new solution, improve basic fund renovation.
Nmap planned followings in next 10 years:
● Nmap Scripting Engine – NSE developed 131 scrpits in the middle of the 2010. It`s 68% more than previous year. NSE scripts increased and widen in every year. As a development team working on to reach more than 500+ official NSE script in upcoming year.
● Scanning web sites – Nmap`s another goal is examining with web direction. First development has been started such as detecting different services working on which ports number, recognizing hidden services and finding catergorize. Now new services working as a HTTP protocol and its recognized with name, protocol numbers by the URL line. Nmap NSE scrips has already included web exam additions to itself. Development team working on to add http brute force password cracking, HTML/XML parser, web applica and proxy port examiner additionally.
● Online scanning web service – As developer mentioned they are working on to create opportunity for customer check network from cloud estimation, own estimation machine, examine according to scheduled date and send result through the email by signal.
Followings are advanced plannings :
- Create ZenMap version to 5 language choices with international support.
- Install additional trail system.
- Add operation system, version detector NIST Common Platform Enumeration standard system and other equipments.
- Create video about Nmap trainging lesson, introduce it to people .
- Soon ZenMep will have additional function interface with choosing intermediate script and script argument.
Work method
Install Nmap program
Go to https://nmap.org/download.html download and install for you current operating system that you are using.
Nmap included widely used system based Debian, Redhat.
Install for Debian base operating system following command should run.
# sudo apt-get install nmapInstall for Redhat base operating system following command should run.
# yum install nmap Read Nmap program output:
nmap [ ...] [ ] { }When you give command above command should be used writing options with checking types, present host name or ip address.
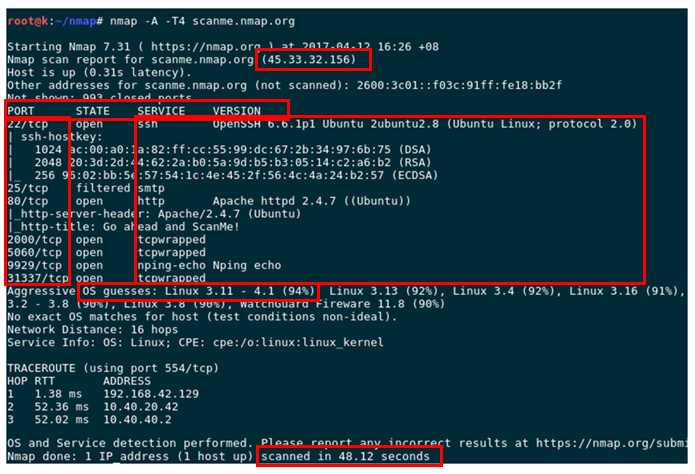
For the above output:
The ip address in which the domain or web is located. At what time the host was examined. Record Information about reverse dns and dns. Нийт хаалттай портуудын тоо. Number of total closed ports, Nmap basic information, service version. Also, depending on the choices its able to see many different types of detailed information. For instance the host operating system, version etc ...
Regular examining types:
There are a few types of regular examining, When Nmap network had TCP connection it could examine with [-sT], SYN scanning [-sS] options. .
TCP connect () Scan [-sT] - This is the examine type which long distance host connected. Using threeway handshake process is examined between two systems. Modern fire wall used to detect SYN packets, Nmap receive and process SYN packet information by own method.
FIN, Null and Xmas Tree Scans [-sF, -sN, -sX] - ХRST send packet information if host or port connection will not be done. FIN idea examine only based on the FIN flag. FIN and URG examine based on the PUSH flag. Null idea examines without any flag and send packet.
Ping Scan [-sP] - This type shows only online network or active host information and examines based on ping request. Send ICMP ECHO(ping request) request to the system. If the system is online, ICMP ECHO REPLY receive response. If the ICMP is blocked Nmap send TCP. SYN send ACK through port.
UDP Scan [-sU] - This option is used to check open UDP ports. UDP send packet through the system.. If the ICMP Port Unreachable, it means the port is closed. Any other time the port is open.
IP Protocol Scans [-sO] - This idea detects either support IP protocol or not and examine on the IP protocol. Nmap send IP packet without adding any header. At this point if you receive ICMP Protocol Unreachable message, it seems protocol is not used and any other time it will be open. But all hosts don’t send above message such as AIX, HP-UX and fire wall.
Version Detection [-sV] - This idea is used to detect what service is going on the system, open ports information, and important information about product name and version. Attaching with this idea you could use A option. This option is used to publish operating system and find its detailed information about version.
ACK Scan [-sA] -
This idea is often used to check host with fire wall and examine through the systems with fire wall. Send ACK packet to host for checking. If received RST response this means the port is unfiltered which means it doesnt filtered by fire wall. if it wont receive response it is filtered by fire wall. Usually this ideas is used when SYN packet is filtered by the fire wall.
Window Scan, RPC Scan, List Scan [-sW, -sR, -sL] - However, TCP window scan is similar to ACK, it is the type that detects open ports and either it is filtered or unfiltered. RCP scan is more suitable to use with other types of exams and often used to get detailed information about what program is working, ongoing service and its version number.
Timing and Hiding Scans - dependin on the internet speed, checking process will not be same as other. However, Nmap will give you a chance to provide faster and powerful examining. This idea is expressed by T- parameter. A-T or A-5 are both available. It sends in 5 minutes. A-T or T0 are also available. It is the estimated time when you examining super fast network.
FTP Bounce - Ftp protocol supported on proxy by RFC 959 standart. Modern ftpds doesn`t work on it, but if you use Nmap the ftp server could be detected.
Turning Off Ping - Nmap –P0 option closes ICMP ping, but PT is option to use TCP Pings. There two important reasons not to use Ping:
When you are using Ping while examining something, it sends lots of information.
Ping response is not sent when you checked Nmap host.
PU option send UDP packet and made Ping. Also there are -PE (Standard ICMP Echo Request), -PP (ICMP Timestamp Request), -PM (Netmask Request) and –PN options.
*Other Nmap options
IPv6 - In Nmap program there are six options work supporting IPv6 protocol.
Verbose Mode- NIn Nmap program has procedure to show detailed information about –v exam.
Resuming - During the process of examining you could use resume option to renew declined command or read file.
Fast Scan -F – F option check all 65535 ports with speed
Time-To-Live -By ttl option to set time-to-live in IPv4 packet .
Nmap NSE
Nmap Scripting Engine (NSE) is most powerful and flexible part of the Nmap program. It gives opportunity for customer using network tasks in wide range. Beside of the Nmap, its scripts work in parallel mode even faster and efficient. Also there is a chance for user develop, change scripts in their need and use it directly.
Example of using Nmap Program
1. Check any host or Ip address
# nmap google.com
# nmap 192.168.56.101Normal output:
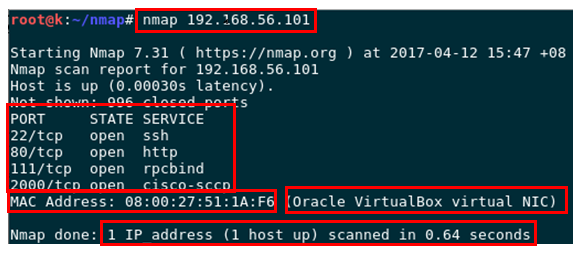
2. Check a few Ip address or subnet
# nmap 192.168.1.1 192.168.1.2 192.168.1.3
# nmap 192.168.1.0/24
# nmap 192.168.1.1,2,3
# nmap 192.168.1.1-10Also using wildcard as known as * check all possibilities
# nmap 192.168.56.*Normal output:
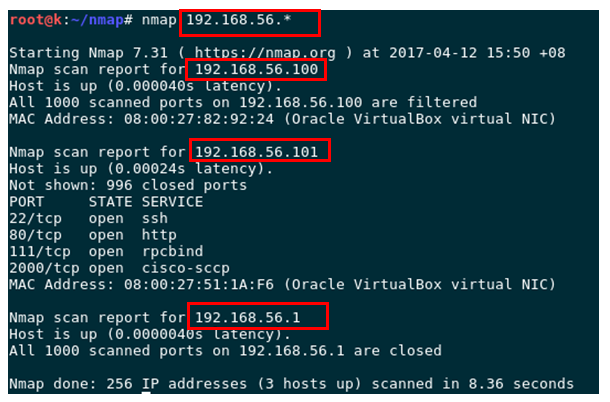
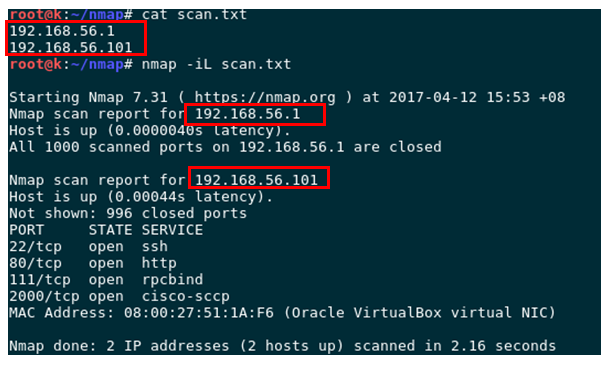
3. Check hosts written on the file
The file should be typed in sequential format in the nmap read-only format.
# nmap –iL hostlist.txt Normal output:
4. Check host or network is protected by fire wall
# nmap –sA 192.168.1.15. Check server and equipments working on server
# nmap –sP 192.168.1.0/246. Immediate examine
# nmap –F 192.168.1.1*7. Check specially chosen port
Check 80 ports
# nmap -p 80 192.168.56.101Check 80 port`s TCP protocol
# nmap –p T:80 192.168.56.101Check a few ports at the same time
# nmap –p 80,22 192.168.56.101Normal output:
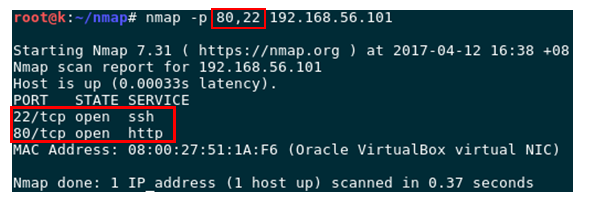
8. Detect service verision working on the port
# nmap –sV 192.168.56.101Normal output:
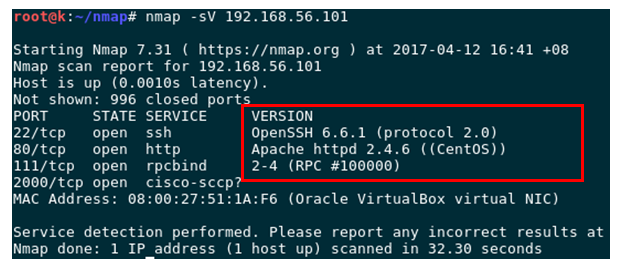
9. Check UDP
# nmap –sU 192.168.56.10110. Write exam outpun to a file
# nmap 192.168.56.101 > output.txt
# nmap –oN output.txt 192.168.56.10111. Examine using NSE script
NSE basic script fund placed at usr/share/namp/scripts folder, you can develop any script you wanted.
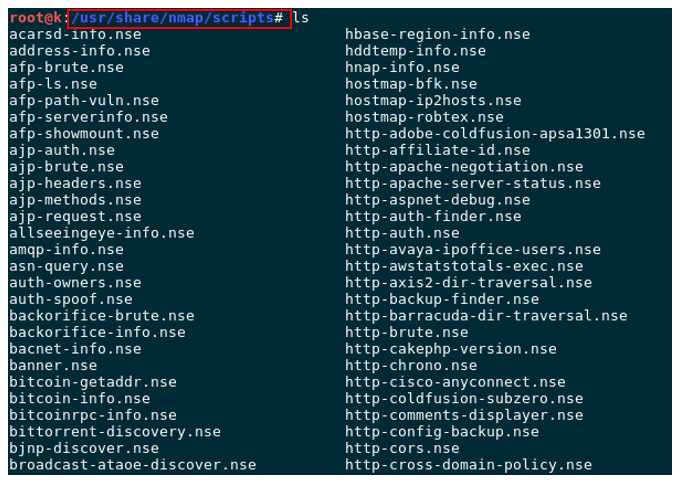
To use thsese scripts add --script=script_name option.
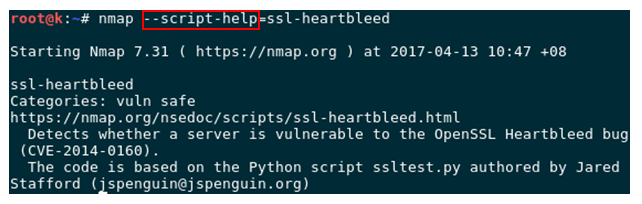
Also you can get the script information by –script-help=script_name option.
Normal output:
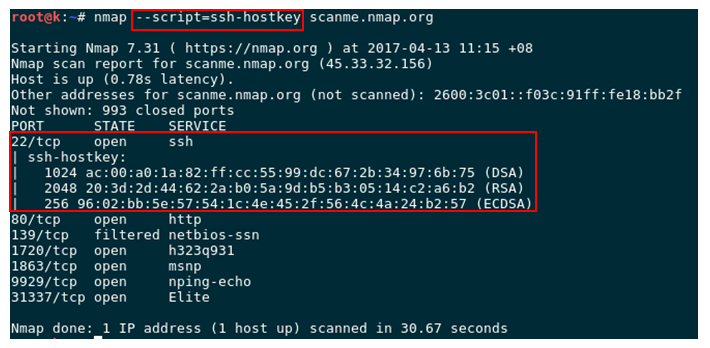
The is the example of used ssh-hostkey script
Normal output:
In conclusion, Nmap is the Open source software that collects detailed information about host or network using normal and flexible command, furthermore it has a chance to do security exam based on the information that used additional “nse” script fund.
Useful link: